As an IT professional, you know that cybersecurity threats are evolving every day. Hackers are finding new ways to infiltrate networks, steal data and disrupt operations. Bad actors often accomplish their goals by exploiting vulnerabilities, and they’re picking up the pace. The Verizon Data Breach Investigations Report 2024 highlighted a 180% rise in attacks that exploit vulnerabilities.
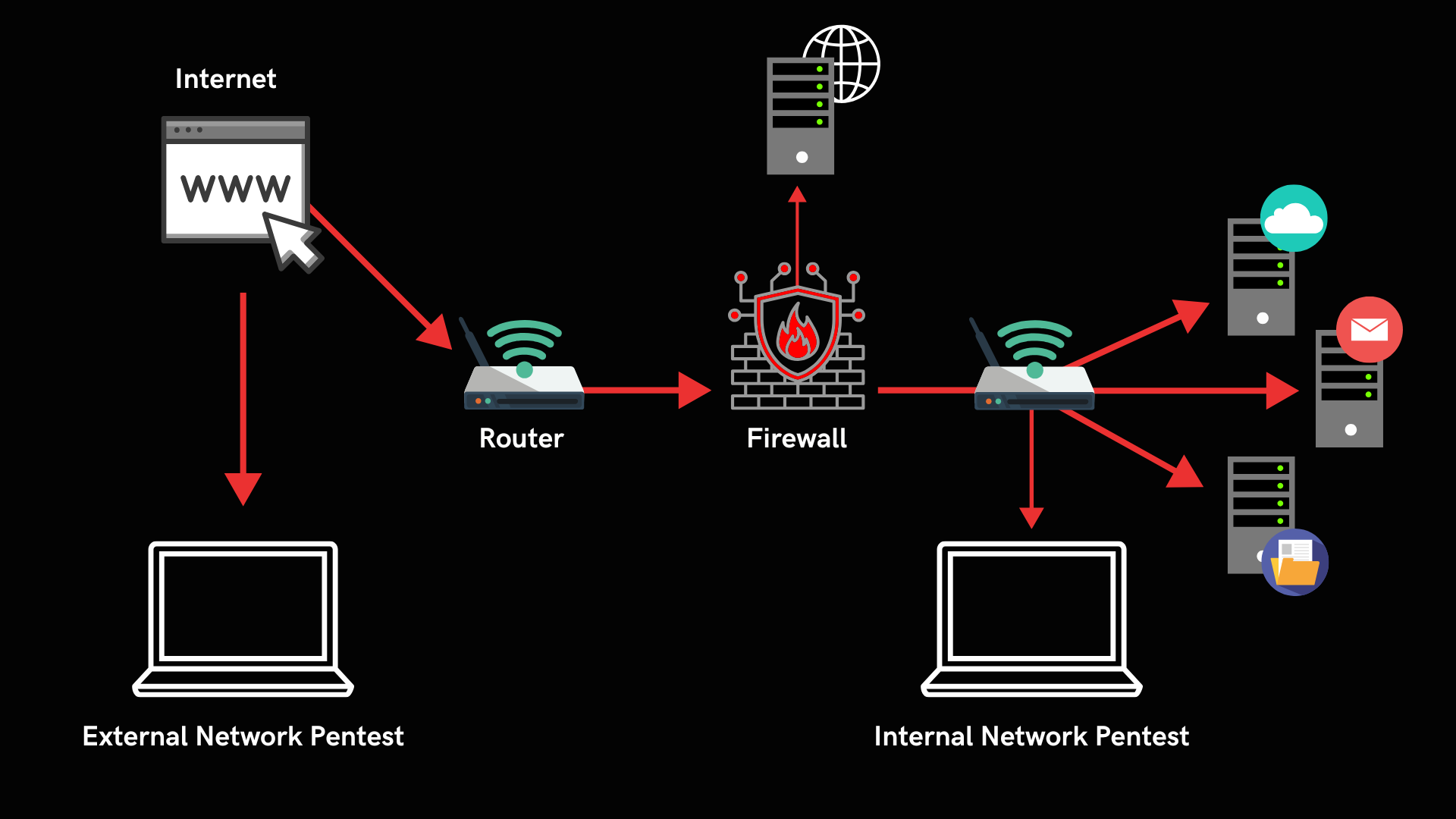
One of the most effective ways to stay ahead of these threats? Regular network penetration testing or pentesting. There are two general types of pentesting: internal and external. But what’s the difference between these two types of tests, and when should you use each? Let’s break it down.
Internal Network Penetration Testing: Looking Within
Internal network penetration testing mimics the actions of an attacker who has gained access to your internal systems. Whether it’s through a malicious insider, compromised credentials or a breach in physical security, this test helps identify vulnerabilities that could be exploited from within your network.
Here's how an internal network penetration test typically works:
- Access to the internal network: The tester starts from a position similar to an insider (like an employee) like someone who has gained unauthorized access might. This could be through a physical connection or a VPN.
- Scanning and reconnaissance: The tester scans the internal network to identify devices, services and open ports. This helps map out the network's structure and potential points of attack.
- Exploitation: After identifying vulnerabilities, the tester attempts to exploit them to gain deeper access, elevate privileges or steal sensitive information. This could include exploiting unpatched software, weak passwords or configuration issues.
- Lateral movement: Testers may try to move across the network, escalating their privileges or accessing different systems, mimicking a real attacker's behavior.
- Reporting: Finally, the tester documents all vulnerabilities discovered, their severity and potential impacts. They also provide recommendations for remediation to improve the network's security posture.
Primary Goals:
- Identifying internal vulnerabilities like weak user privileges, poor network segmentation and unpatched software within firewalls.
- Evaluating insider threat risk by testing what damage a malicious attacker or compromised employee could inflict. This could involve privilege escalation, malware spreading and credential theft.
- Examining systems such as file servers, Microsoft Exchange and Active Directory for configuration weaknesses that could allow attackers to gain unauthorized access.
When to conduct internal network penetration testing:
- After deploying new internal infrastructure.
- Following major updates or reconfiguration changes.
- After a security incident or breach.
- To assess insider threats and lateral movement risks.
- For compliance with regulations like HIPAA or PCI-DSS.
- As part of routine security health checks (at least once a year).
Why you should do it:
- Perimeter defenses aren't enough: An attacker only needs to find one vulnerability to gain entry, and once inside, an unsecured internal network can quickly become a playground for privilege escalation and data exploitation.
- Critical for uncovering hidden risks: Internal network penetration testing reveals critical flaws in network segmentation, access controls, and system configurations, showing the real-world impact of internal attacks.
- Compliance is mandatory: Regulations like PCI DSS require annual internal network and segmentation testing, or every six months for service providers.
Internal network pentests are all about finding the gaps in your internal defenses before an attacker does. Think of it as a way to ensure that, even if someone gets in, they can’t do much damage.
External Network Penetration Testing: Protecting Your Perimeter
On the other hand, external network penetration testing mimics an attack from outside the organization. It focuses on your organization’s public-facing assets, those systems and services that are exposed to the internet like websites, email servers and file transfer systems. The goal is to simulate how an outside attacker would attempt to breach your network from the outside.
Here's how an external network penetration test typically works:
- Reconnaissance: The tester gathers information about the target from publicly available sources (called open-source intelligence or OSINT). This includes domain names, IP addresses, public servers and other services exposed to the internet.
- Scanning: The tester scans the organization's external network for open ports, running services, and software versions. This helps identify potential entry points and vulnerabilities like outdated software or misconfigured services.
- Vulnerability Identification: Based on the scanning results, the tester looks for known vulnerabilities or misconfigurations that could be exploited. These might include weaknesses like unpatched systems, default credentials or misconfigured firewalls.
- Exploitation: If vulnerabilities are found, the tester attempts to exploit them to gain unauthorized access to the system. This could include attempting to bypass authentication mechanisms, gain remote access or extract sensitive information.
- Reporting: The tester documents all findings, including discovered vulnerabilities, the methods used to exploit them and potential impacts. They also provide recommendations on how to mitigate these risks, such as patching, configuration changes or adding security controls.
Primary Goals:
- Assessing perimeter security by identifying vulnerabilities in public-facing systems, firewalls and routers.
- Mimicking real-world attacks that an outsider without prior knowledge of the network could attempt. This could include attacks on internet-facing services such as FTP servers and administrative features of applications.
- Protecting against automated scans and attacks by malicious actors who regularly probe public networks for exploitable weaknesses. For example, a recent study shows that cyberattacks occur every 39 seconds globally, emphasizing the constant threat to internet-facing systems.
When to conduct external penetration testing:
- Before launching new websites, APIs or cloud applications.
- After significant updates or changes to public-facing systems.
- To meet compliance with standards like ISO 27001 or GDPR.
- Following the detection of suspicious external traffic.
- After a breach to strengthen your security posture
- To establish a security baseline and assess your external security posture
Why you should do it:
- Secures the network edge: The perimeter is the first line of defense against the open internet. External penetration testing ensures this barrier remains strong, preventing unauthorized access to your systems.
- Identifies exploitable vulnerabilities: By simulating real-world attacks, external penetration testing reveals weaknesses that attackers could use to breach your network and access sensitive data.
- Proactive risk mitigation: Regularly testing and improving your external defenses allows your organization to take preventive measures before any incident occurs, significantly reducing risk.
External pen tests are essential for identifying weak spots in your outer defenses, preventing unauthorized access to your systems from the outside world.
How Often Should You Conduct Network Penetration Testing?
While every organization is different, a solid rule of thumb is:
- Internal Pen Tests: At least once a year, and ideally quarterly, to stay aligned with industry best practices. More frequent tests are recommended after significant changes or security incidents to ensure your systems remain secure.
- External Pen Tests: Every 6-12 months, with quarterly testing being ideal to meet industry best practices, especially after public-facing systems undergo updates.
Industries like healthcare and finance, where the stakes are higher, may require even more frequent testing to comply with regulations and mitigate risks.
Why Network Penetration Testing is a Must
No matter how strong your cybersecurity measures seem, there’s always the possibility of something slipping through the cracks. Regular penetration testing is like a "stress test" for your security defenses— it reveals hidden vulnerabilities before they’re exploited by the bad guys.
By consistently testing both your internal and external networks, you’re not only strengthening your defenses but also gaining valuable insight into where your security strategy needs improvement.
In a world where cyber threats are ever-present, network penetration testing is a must-have—a proactive way to protect your data, reputation and bottom line. Investing in these tests not only protects your infrastructure but also ensures long-term resilience against both internal and external threats.
vPenTest: A Game-Changer in Network Security
In the Kaseya Cybersecurity Survey 2024, we asked IT professionals about the barriers that they faced that prevented them from engaging in more regular penetration testing. Our survey respondents told us that Cost, specifically budget constraints, is the primary roadblock to pentesting (58%). Resource limitations (18%) and IT staffing issues (12%) are also challenges that must be overcome.
vPenTest changes the game.
With vPenTest, you can bring penetration testing in-house, running frequent monthly tests instead of yearly assessments. However, cyberthreats are evolving faster than ever before, with new vulnerabilities and zero days popping up every day. Testing once per year just doesn’t cut it anymore.
vPenTest offers an automated, easy-to-use solution that drastically cuts the expense of testing, minimizes disruption and makes the process easy without compromising quality. Proactive testing with vPenTest makes keeping your network secure is easier and more cost-effective than ever.