In today’s challenging economy, no company can afford to fall victim to cybersecurity trouble like a cyberattack or data breach. Companies can invest in a wide array of cybersecurity solutions to help safeguard their networks and data, but how can they be sure that they’re making the right security choices? Even with a solid investment in cybersecurity, a company could still have dangerous vulnerabilities that cybercriminals can exploit. Enter penetration testing. This smart investment can be a company’s cybersecurity secret weapon.
One cybersecurity incident or cyberattack can be a financial disaster
Just one cybersecurity incident can be punishingly expensive. In our Kaseya Security Survey Report 2023, we surveyed IT professionals about their company’s cybersecurity goals and experiences in 2023. Some of those cybersecurity experiences were very expensive. Over half of our survey respondents (56%) said that their organization has lost $50,000 or more in a cybersecurity incident. Some businesses sustained an even harder hit. Just over one-third of respondents (39%) lost $100,00 or more, and 21% lost a whopping $250,000 or more. In today’s challenging economy, no business can afford this kind of monetary loss, making cybersecurity safeguards like penetration testing mission critical.
If you’ve experienced a cybersecurity incident, what was the total cost to the business, including lost revenue, lost productivity and recovery?
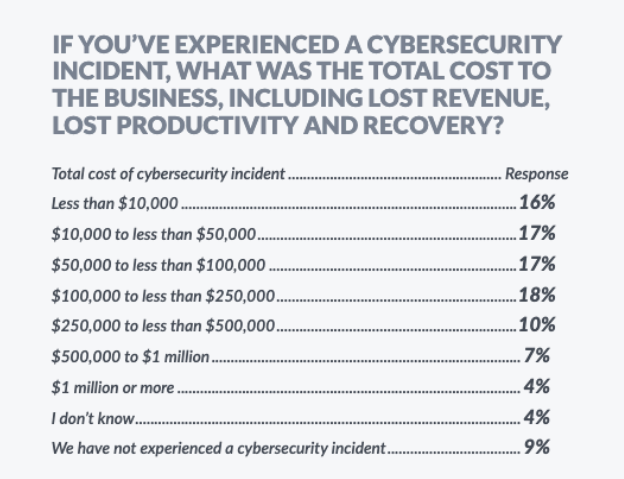
Source: Kaseya Security Survey Report 2023
https://www.idagent.com/resources/kaseya-security-survey-report-2023/
Penetration testing can help companies avoid expensive cyberattacks
One effective way for companies to make sure that they’ve got a sturdy defense against cyber threats in place is to test those defenses. Testing can be done through vulnerability assessments and penetration testing. Although these two methods sound similar, they are not the same.
A vulnerability assessment involves the systematic identification, quantification and prioritization of potential security weaknesses in a system, network or application. It aims to provide a comprehensive overview of vulnerabilities without actively exploiting them.
A penetration test, or ethical hacking, goes a step further by simulating real-world attacks to exploit identified vulnerabilities and assess the effectiveness of existing security controls. Pen testing takes assessment a step further by actively exploiting a company’s vulnerabilities with the aim of showing companies quickly and accurately which of their security weaknesses matter the most.
A vulnerability assessment and a penetration test are both critical components of cybersecurity, but they serve distinct purposes within the realm of proactive security measures. While a vulnerability assessment is more focused on discovering and cataloging potential weaknesses, a penetration test emulates the actions of a malicious actor to evaluate a system or network’s defensive readiness and uncover any potential weaknesses that may not be apparent through a static assessment alone. Penetration testing is a proactive and systematic approach to identifying and addressing security vulnerabilities, contributing significantly to an organization's overall cybersecurity resilience.
Companies need to pick up the pace and start frequently testing their defenses
IT security testing is an invaluable tool for organizations to employ to find weaknesses in their security buildout, and most of our respondents are putting some type of defensive testing like vulnerability assessments or pen testing to work for their organization. Over half of our survey respondents (52%) said that their company conducts assessments two to four times per year. Another fifth (20%) said that their employer conducts assessments only once per year. Even worse, 8% of respondents conduct assessments only every two to five years, allowing dangerous weaknesses that could translate into successful cyberattacks to linger unchecked
In the past, cost was a barrier to increasing the frequency of IT security testing like vulnerability assessment or network penetration testing, but that’s not the case anymore. Automated solutions are a game-changer, making running more frequent assessments including pen tests easy and affordable.
Approximately how frequently does your organization conduct IT security vulnerability assessments?
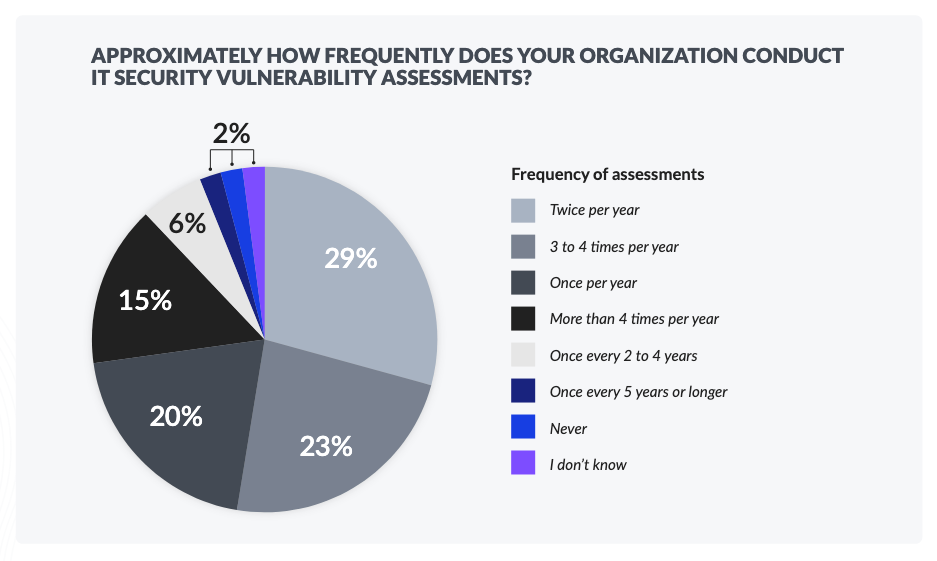
Source: Kaseya Security Survey Report 2023
https://www.idagent.com/resources/kaseya-security-survey-report-2023/
Businesses get 6 big benefits from penetration testing
Among the arsenal of cybersecurity measures, penetration testing stands out as a proactive and indispensable practice. While many businesses have traditionally viewed penetration tests as periodic necessities for compliance, the fast-evolving cyber threat landscape dictates more caution these days. With new zero-day threats and novel cyberattacks emerging daily, a yearly or even quarterly pentest just can’t keep up, leaving businesses open to dangerous and potentially expensive cyberattacks. Monthly penetration testing is the answer – and it's not even expensive anymore. Businesses gain unbeatable benefits from monthly pentesting including:
1. Identifying Vulnerabilities in Real Time:
Frequent penetration tests provide a dynamic and real-time assessment of a company’s digital infrastructure. Cyber criminals are agile, adapting their methods and tools swiftly and quickly exploiting new vulnerabilities. Regular testing allows your organization to stay ahead of the curve by identifying and addressing weaknesses promptly, minimizing the window of opportunity for potential attackers.
2. Adapting to Evolving Threats:
Cyber threats are not static. They evolve constantly, becoming more sophisticated and difficult to combat over time. Conducting monthly penetration tests enables a company’s cybersecurity team to adapt their strategies based on the latest threat intelligence. This proactive stance ensures that an organization’s defenses are always one step ahead of the rapidly changing threat landscape.
3. Enhancing Incident Response Preparedness:
Time is of the essence to contain the damage in an incident response. Frequent penetration testing serves as a powerful tool for refining a company’s incident response capabilities. Simulating various attack scenarios allows an organization to fine-tune its response procedures, helping security teams become more adept at detecting, containing and mitigating potential threats. This preparedness is invaluable in the event of a real cyber incident.
4. Meeting Compliance Requirements:
In many industries, regulatory compliance mandates regular security assessments. Frequent penetration tests not only ensure compliance with these regulations but also demonstrate a commitment to cybersecurity best practices. This proactive approach not only safeguards your organization but also fosters trust among clients, partners, and stakeholders.
5. Optimizing Resource Allocation:
Regular penetration testing helps organizations optimize resource allocation by pinpointing specific areas of vulnerability. Instead of deploying broad-stroke security measures, businesses can focus their efforts and resources on the most critical areas identified through frequent testing, maximizing the impact of their cybersecurity investments.
6. Safeguarding Reputation and Customer Trust:
A security breach can have far-reaching consequences, including reputational damage and a loss of customer trust. Frequent penetration tests not only reduce the likelihood of successful cyberattacks but also demonstrate a commitment to maintaining the confidentiality and integrity of customer data, enhancing trust among clients and stakeholders.
Embracing a proactive approach to cybersecurity through regular assessments empowers organizations to fortify their digital fortifications, adapt to emerging threats, and maintain a resilient defense against the ever-evolving landscape of cyber risks. As businesses continue to navigate the complexities of the digital realm, the investment in frequent penetration testing emerges not only as a necessity but as a strategic imperative in the ongoing battle against cyber threats.
