Every Breach Starts Small, But Spreads Fast
It only takes one mistake for an attacker to gain a foothold. One click on a phishing email, one missed patch, or one default password left in place is often all it takes. The problem is not just the initial mistake, but how far it spreads across your systems. This is why cyber risk is now considered the number one threat to business survival.
The numbers tell the story. 60% of SMBs close within six months of a breach. Yet companies still spend more on physical security than on pentesting, and many insure themselves against natural disasters while ignoring cyberattacks even though the chance of being hacked is nearly 50%. The reality is clear: without testing, security tools only provide a sense of safety, not true protection.
Why Pentesting is the Only Way to Prove Security
Traditional defenses like firewalls, endpoint detection, and multifactor authentication are all necessary, but none of them prove your systems can contain an attack. Pentesting does what nothing else can: it replicates an attacker’s methods, identifies weaknesses, and demonstrates how far a compromise can spread.
This is the difference between one compromised account and a company-wide breach. Pentesting doesn’t just highlight issues it shows you exactly what attackers would exploit and gives you the opportunity to fix those weaknesses before they’re used against you. Instead of waiting to respond to an alert after an attack has already begun, pentesting is proactive: it identifies lateral movement paths, privilege escalation opportunities, and data exposure risks so they can be remediated in advance. The result is prevention and containment before an incident ever happens, not reaction after the damage is already underway.
And when it comes to real-world results, pentesting uncovers the risks that scanners miss. According to Vonahi Security’s 2025 Top Pentest Findings Report, the three most common internal network vulnerabilities are:
- MDNS Spoofing (60.5%) – Attackers spoof responses and trick devices into leaking credentials.
- NBNS Spoofing (57.9%) – Legacy Windows broadcast behavior that lets attackers steal NTLM hashes.
- LLMNR Spoofing (52.0%) – A Windows DNS fallback that enables spoofing and credential capture.
The common pattern across these findings? They are not patchable CVEs. They are protocol and configuration weaknesses. Scanners often flag them as “informational,” but attackers use them to steal credentials and move laterally. Even when fixed, they frequently resurface due to new devices, default settings, or configuration drift. Pentesting is the only way to identify these weaknesses in action and validate that fixes hold over time.
Why Once-a-Year Testing Isn’t Enough
The threat landscape changes every day. New users, new systems, and new vulnerabilities constantly create fresh opportunities for attackers. That’s why annual pentesting is no longer sufficient. By the time the report is delivered, it is often outdated. A single test each year might satisfy compliance, but it does not keep you secure.
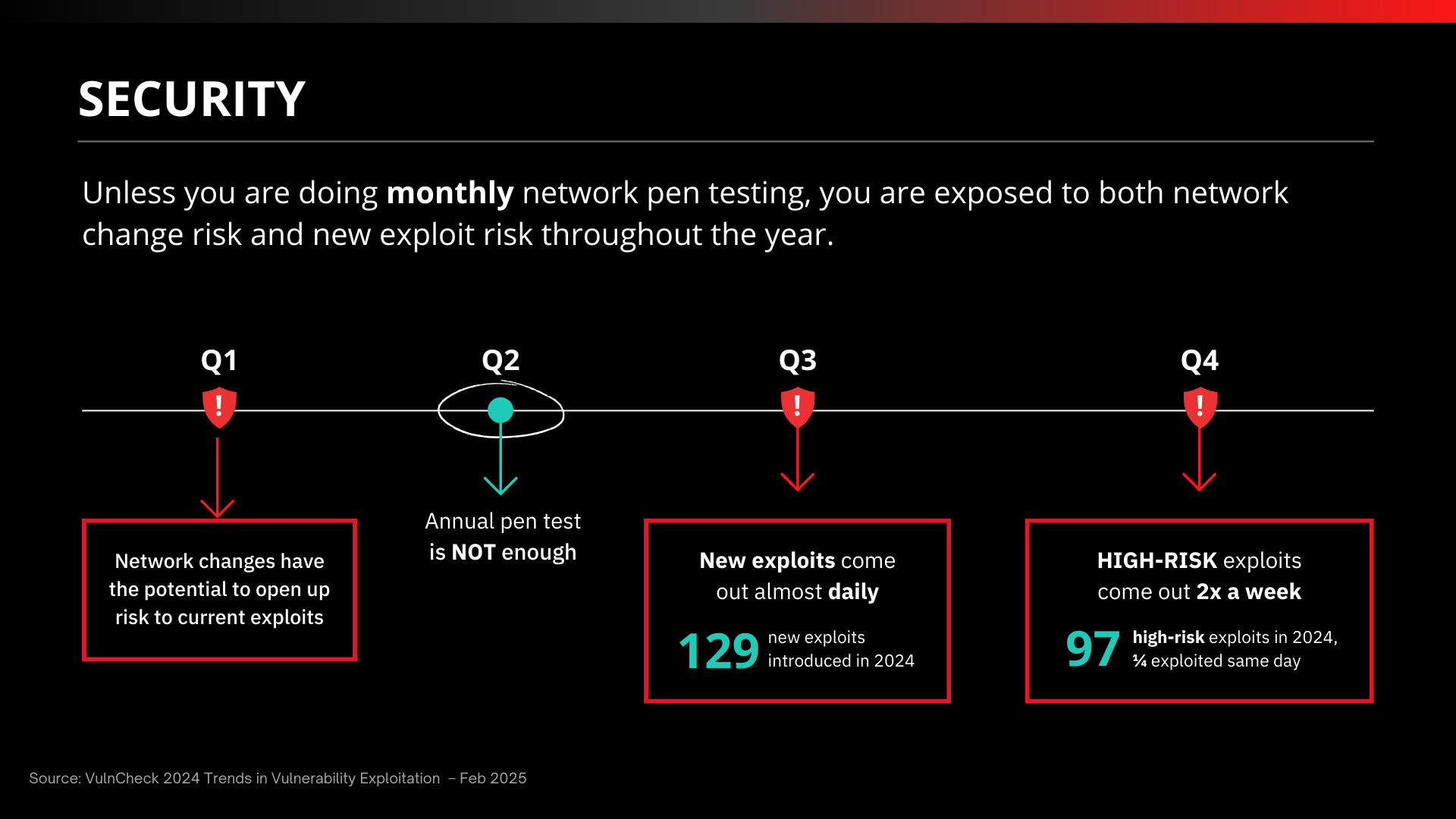
This is where continuous network pentesting becomes the new standard. Testing frequently, and often automatically, ensures that defenses are validated throughout the year instead of just once. Without it, organizations are relying on guesswork in between long testing cycles.
vPenTest: Making Pentesting the #1 Security Control
Manual network pentests have traditionally been slow, expensive, and compliance-focused. They were designed for auditors, not attackers. vPenTest changes that. By automating network penetration testing, vPenTest delivers frequent, real-world simulations at a fraction of the cost.
Traditional manual pentests often cost $10,000 to $20,000 per engagement and only provide a single, expensive snapshot in time. vPenTest delivers continuous, monthly testing and remediation testing at roughly half the cost. In other words, why pay double for one test when you can validate your defenses every month for less?
With vPenTest, you get real-time validation that your defenses can contain a breach versus a point-in-time snapshot of your risks, and on-demand remediation testing as your systems evolve. This is why more than 27,000 organizations have trusted the platform for their internal or external network pentesting needs.
It is not just about meeting compliance; it is about proving security. With vPenTest, businesses gain the independence auditors require, the assurance executives demand, and the protection attackers cannot bypass.
Do Not Assume, Validate
Cybersecurity is not about hoping your defenses will hold. It is about proving that they will. Pentesting should be your number one security control because it transforms uncertainty into evidence, shows how far a breach could spread, and ensures that one mistake does not turn into a business-ending event.
The reality is simple: attackers are constantly looking for the one gap that will let them in. The organizations that survive are the ones that validate their defenses before adversaries do. Pentesting gives you the proof, the visibility, and the confidence that your security program can withstand real-world threats.
In the end, the difference between resilience and ruin often comes down to a single question: did you test your defenses before an attacker did?

Ready to see how continuous, automated network pentesting can transform your security strategy? Schedule a demo of vPenTest and start proving your defenses work.
