It is still all too common to find unnecessary services and protocols that are public-facing on the internet. In many cases, these services are exposed by accident, such as through a misconfiguration, or even intentionally.
In recent months, attackers have been utilizing Remote Desktop Protocol (RDP) to infiltrate systems and distribute ransomware to networks. RDP is a proprietary network protocol that allows an individual to access and control the resources and data of a computer over the internet. Previous ransomware attacks, such as CrySiS , CryptON, and SamSam have been utilizing RDP attacks to successfully compromise networks.
According to US-CERT, cybercriminals are attacking RDP and, oftentimes, selling the stolen information on various dark web underground marketplaces [1].
Twitter post [2]:

Shodan Research
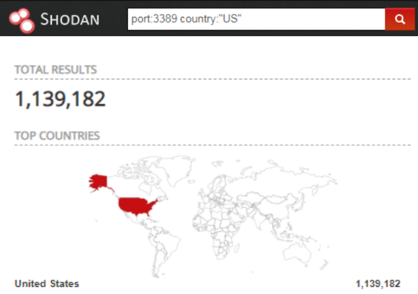
A quick overview of Shodan, a search engine for Internet-connected devices, shows us that RDP is still a very popular public-facing administrative service protocol that is widely utilized across the internet. In the United States, Shodan shows around 1,139,182 public facing systems utilizing the RDP port 3389/tcp.
Search Filter: port:3389 country:”US”
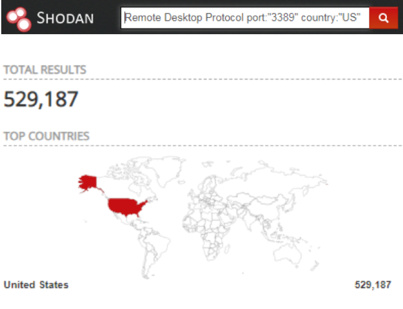
A more defined search looking for strings related to RDP with the port 3389 in the United States show us around “529,187” exposed RDP services.
Search Filter: Remote Desktop Protocol port:”3389″ country:”US”
What are some concerns?
- Authentication Attacks – Depending on the services exposed, an attacker may be able to perform authentication-based attacks that attempt to guess passwords for valid user accounts. The strength of the accounts targeted during these attacks depend on the complexity of the users’ passwords.
- Information Disclosures – Some services may disclose information that should only be known to trusted individuals, such as internal IP addresses, domain name information, etc.
- Man-in-the-Middle (MitM) Attacks – If there is an insecure protocol exposed to the Internet, an attacker could potentially perform a MitM attack against the vulnerable service and a connecting client. Say, for example, an administrator is trying to Telnet or FTP into a public FTP server and an attacker is scanning all traffic. Those credentials will get exposed.
- Exploitation – Depending on any of the weaknesses discovered, such as those listed above, an attacker may be able to successfully exploit and gain access to the remote server, which could potentially lead to a data breach.
What can be done to fix these issues?
Generally speaking, your organization should perform a review of its external environment on a regular basis. Throughout the year, it is not uncommon for an administrator to make an unintended change to the firewall and accidentally expose additional services. We actually see this happen from time to time when we’re monitoring clients subscribed to Attack Surface Intelligence (ASI).
These are some mitigation strategies that should be followed:
- Restrict services that are not required on the public Internet for business operations. For services that are indeed required, such as RDP, place these services behind a VPN.
- If a VPN service is implemented, ensure that two-factor authentication (2fa) is implemented.
- Configure all passwords to adhere to strong password complexity requirements. For services which cannot be controlled systemically, enforce these procedures through configuration hardening policies.
- Regularly apply patches that affect both native and third-party software. Legacy software should be restricted as much as possible.
References:
[1] https://www.ic3.gov/media/2018/180927.aspx
[2] https://twitter.com/USCERT_gov/status/1045694918025531393
About Vonahi Security
Vonahi Security is a cybersecurity consulting firm that offers modern consulting services to help organizations achieve both compliance and security best practices. With over 30 years of combined industry experience in both offensive and defensive security operations, our team of certified consultants have experience working with a significant number of organizations, industries, networks, and technologies. Our service expertise includes Managed Security, Adversary Simulations, Strategy & Review, and User Education & Awareness. Vonahi Security is headquartered in Atlanta, GA. To learn more, visit www.vonahi.io
Stay Informed
