Amateurs hack systems, professionals hack people.
- Bruce Schneier
From phishing and BEC to evasive spear phishing and VEC
When companies are investigating the weak points in their cyber defenses, they must look beyond their IT infrastructure. In most cases, an organization’s biggest security vulnerability does not stem from the machines on its network, but from people on the payroll. And because this is common knowledge to threat actors, social engineering attacks that target employees generally constitute a bigger threat to businesses than cyber campaigns that directly attack computer systems. The two most common examples of social engineering attacks are phishing campaigns and business email compromise (BEC) scams. While phishing is the top threat action leading to security breaches, as Verizon’s 2019 Data Breach Investigations Report (DBIR) shows, BEC scams are a $26 billion headache for organizations around the globe, according to the Internet Crime Complaint Center (IC3) of the US Federal Bureau of Investigation (FBI). As bad as this sounds, things are actually getting worse, because cybercriminals are launching increasingly sophisticated and targeted variations of these attacks that are nearly impossible to detect. A recent bulletin[pdf] by Glasswall and Forcepoint describes evasive spear phishing as the latest incarnation of phishing attacks, and a report by Agari warns of a new variation on BEC dubbed vendor email compromise (VEC). Let’s have a look at these new attack techniques.
What is evasive spear phishing?
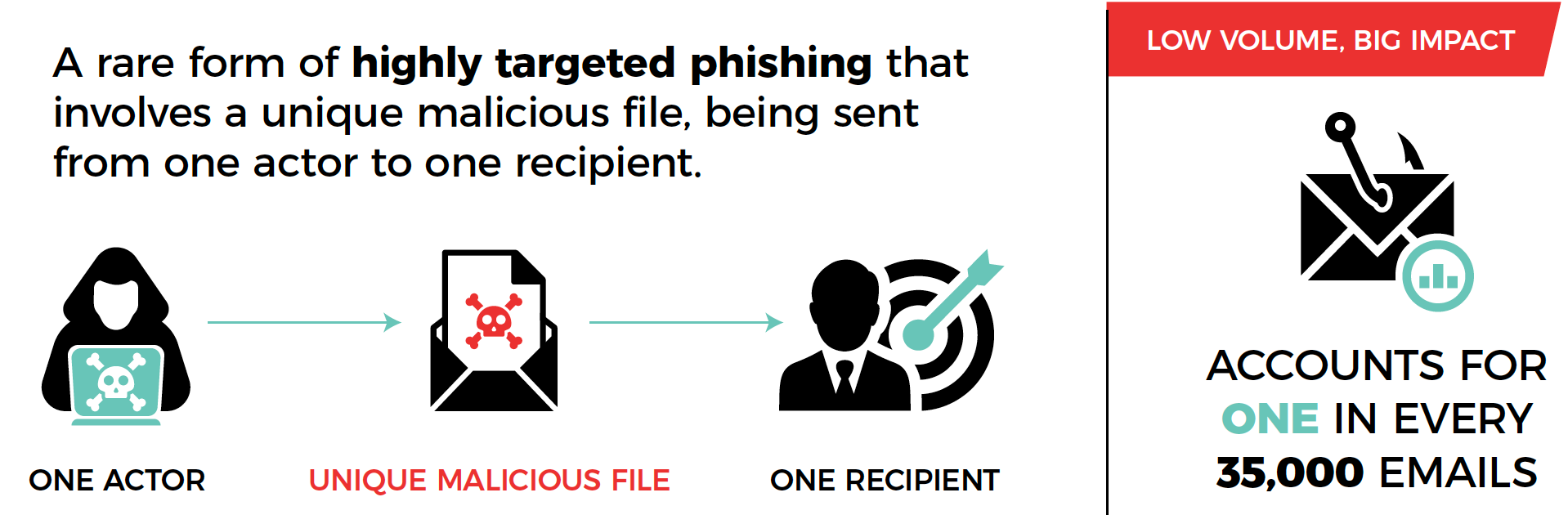
As we discussed in a previous blog post, phishing is a social engineering attack that involves manipulation as well as technological deception (spoofing). The aim of the attacker is to obtain sensitive information from a victim by pretending to be a company or person that the victim trusts. Targeted phishing is called spear phishing. According to Glasswall and Forcepoint, evasive spear phishing is a rare form of highly targeted phishing that involves “a unique malicious file, being sent from one actor to one recipient.” This threat accounts for just 1 in every 35,000 emails. While this means that evasive spear phishing “represents the lowest occurring threat in terms of volume,” it can have devastating financial and reputational consequences for the targeted firm. Like category 5 hurricanes, evasive spear phishing attacks are extraordinary events, and if your organization gets hit by one, the disruptive impact is likely to be immense. But unlike tropical cyclones, these campaigns are incredibly targeted and really hard to detect. The two main characteristics of a typical evasive spear phishing message are:
- The content is very specific and highly relevant to the targeted employee and their company. This is because threat actors spend weeks or even months researching a victim before launching an attack.
- The message contains a malicious attachment with a common file type like .PDF (43%) or a Microsoft Binary format (’97-‘03) Word document (.doc, 35%). The likelihood of detection is much lower than that of a normal spear phishing attack.
The combination of a tailored message and an attachment in a familiar format greatly increases the likelihood that a recipient will interact with the malicious file. Once they do, the attack is almost certain to be successful because anti-virus solutions usually fail to detect the evasive malware embedded in the attachment.
Evasive spear phishing mostly affects a limited number of sectors. The main industries targeted by this threat are:
- Technology (47.6%)
- Legal (24.81%)
- Analyst (11.38%)
- Industrial control systems (8.21%)
- Family fund (4.10%)
- Finance (3.37%)

What is vendor email compromise?
In a textbook business email compromise scam, threat actors compromise or spoof a professional email account in order to masquerade as the account’s owner in communications with the actual target of the campaign, which is often someone working in accounting in either the same organization or at a third party, such as a business client. Most of these attacks aim to deceive the target into carrying out a wire transfer to the threat actor’s bank account. The attacker usually achieves this by informing the target of a change in the impersonated entity’s banking information, while providing the details of an account they control. Vendor email compromise is an especially dangerous variant of BEC that exploits the relationship between companies and their vendors/suppliers.
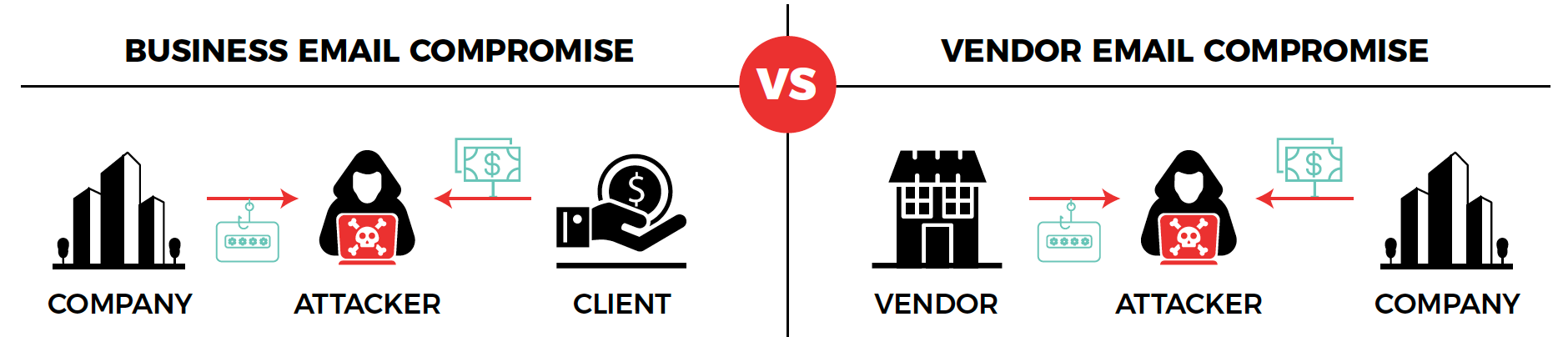
According to Agari, a VEC scam follows the pattern described below:
- Stage 1: Instead of spoofing a business email account, the attackers actually take control of a vendor’s account using login credentials obtained via a (spear) phishing campaign.
- Stage 2: The threat actors configure the compromised account to forward copies of all email communications to an email account they control.
- Stage 3: The scammers take their time to analyze the email communications between the compromised vendor and one of their business customers in order to learn not only how they interact with one another, but also to study the ins and outs of the billing process. This stage can last for months.
- Stage 4: Once the attackers are sure they know everything they need to know in order to convincingly impersonate the vendor, they use the latter’s email or a spoofed account in order to request a phony invoice payment from the customer, while providing the vendor’s “new banking details,” which actually belong to an account they control. Because the attackers know exactly what their fake invoice should look like, as well as what language to use in the accompanying message, the target is almost certain to view their request as legitimate and to transfer them the requested sum.
In essence, what sets VEC apart from traditional BEC attacks, is the extraordinary patience displayed by the attackers and, in line with this, their attention to detail. In this sense, VEC closely resembles evasive spear phishing.
What can you do to protect your organization from evasive spear phishing and VEC?
These sophisticated attacks are difficult to defend against, but adopting the following practices, will go a long way:
- Implement cybersecurity best practices. For more information on this, see our White Paper for small to mid-sized businesses (SMBs). It contains plenty of information that is relevant for larger firms as well.
- Put advanced security solutions in place to detect malicious activity on your network. In the face of evasive malware, basic anti-virus just doesn’t cut it. For more information, check out the White Paper referenced above.
- Always verify requested changes to payment details and other relevant information using a medium other than email. The best method for this is generally a phone or video call.
- Finally, provide phishing awareness training in your organization and carry out phishing simulations on a regular basis. Training sessions should be interactive and must be supplemented with phishing tests that simulate attacks to check if employees are actually applying what they have learned about spotting suspicious emails. It is crucial that the results of phishing tests are carefully analyzed and used to maximize the effectiveness of the security awareness program. This is why Vonahi’s proprietary phishing platform vPhish not only allows organizations to carry out phishing simulations, but also provides detailed information showing what employees interacted with phishing messages, when, and in what way. In addition, vPhish shows statistics on the impact of tests and identifies users that keep falling for simulated scams. This enables companies to optimize their training content and prioritize users or departments that represent the biggest risk.
About Vonahi Security
Vonahi Security is a cybersecurity consulting firm that offers modern consulting services to help organizations achieve both compliance and security best practices. With over 30 years of combined industry experience in both offensive and defensive security operations, our team of certified consultants have experience working with a significant number of organizations, industries, networks, and technologies. Our service expertise includes Managed Security, Adversary Simulations, Strategy & Review, and User Education & Awareness. Vonahi Security is headquartered in Atlanta, GA. To learn more, visit www.vonahi.io
Stay Informed
