What do military strategists, sports coaches, tabletop gamers, and cyber security consultants all have in common? They know the value of the popular adage: “The best defense is a good offense.” In the context of cyber security, this certainly does not mean that businesses should be looking to hack the systems of threat actors. Instead, it refers to the need for organizations to incorporate offensive security in the form of penetration testing, or pentesting, into their cyber security program. As we have discussed in a previous blog post, a penetration test comprises the manual testing procedures executed by a security consultant to identify and exploit security flaws within a client’s environment. But why are pentests so important?
The short answer is that penetration tests allow organizations to assess their cyber security posture based on realistic attack scenarios, which in turn enables them to address issues that would be overlooked if they followed a solely defensive approach to security. Since that sounds a little vague, we wanted to outline some of the main benefits of pentesting in this post.
1: Almost all penetration tests reveal crucial security flaws
The most straightforward argument for pentesting is that it works. In other words, pentesters usually succeed in finding holes in the cyber defenses of the client organization. In fact, a recent study by Positive Technologies found that, in 2018, the client’s internal network was breached in 92% of external pentests, where the security researcher impersonates a threat actor outside of the organization. Even more dramatic were the results of internal pentests, which focus on the damage that a malicious insider connected to the local network could do, as pentesters were able to obtain complete, administrative control of the systems under scrutiny in 100% of cases.
These findings demonstrate two things. The first is that penetration testing is clearly effective in terms of exposing ways in which threat actors could break into and move across your network in order to access, manipulate, damage, or destroy valuable data and systems. The research also points out that companies are simply failing to properly secure their systems. Part of the problem is that many organizations do not adequately prioritize security and therefore do not allocate sufficient resources to it. However, the underlying issue here is that focusing on defensive security alone, like many companies do, is a fundamentally flawed strategy to begin with.
Trying to build a hackproof system and keeping it secure solely by defensive means, like the best practices we outline in our whitepaper for SMBs, is like trying to deliver a flawless manuscript by editing your own work: while it is crucial that you review your writing before submission, you are bound to overlook a few typos and perhaps even more fundamental mistakes. To avoid this, you really need a fresh pair of eyes to look at your work. The best person for the job will be a professional proofreader, who knows exactly how the publisher's reader will review your writing. The same is true for organizations that want to verify how secure their systems really are: they need someone to probe their systems just like an attacker would. The best person for the job? A professional pentester.
2: Penetration tests help against patch fatigue
In addition to the fundamental problems with a purely defensive security program discussed above, there are also practical factors preventing organizations from optimizing their cyber security. One common issue is patch fatigue. Organizations increasingly struggle to keep up with the overwhelming amount of security patches that are constantly being released for newly discovered software and hardware vulnerabilities. Patch fatigue has been a problem for years, and things are only getting worse since the number of reported vulnerabilities keeps on increasing year after year, with the current record from 2018 standing at over 16,500 security flaws, i.e. 45 per day (see Figure 1 below). Even if only 10% of those patches are relevant for your systems, this means that every week, about 32 fixes have to be identified, tested, and installed across your organization, which is a daunting task for most IT departments.
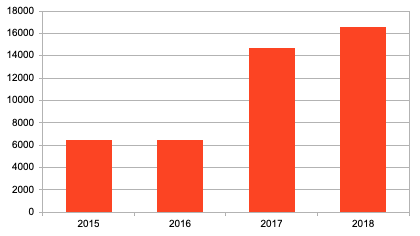
Source: CVE Details
By performing regular penetration tests, companies can identify the most vulnerable elements of their IT infrastructure, so they can prioritize security patches for those systems. For instance, the study quoted above states that, in external pentests, security specialists were often able to breach the network perimeter by taking advantage of vulnerabilities in web applications. 3 out of every 4 discovered penetration vectors (i.e. ways of accessing the local network) stemmed from poorly secured web apps. In these cases, clients could start securing those applications by installing the latest security updates and improving security configurations wherever necessary.
3: Penetration tests expose issues beyond the scope of vulnerability assessments
One way for organizations to find out about the weak links in their cyber security posture is by having a security professional conduct a vulnerability assessment, which means that the consultant will scan their environment in order to detect known flaws that affect their systems. While vulnerability assessments are very useful for companies looking to bolster their security, penetration tests provide a lot of additional value. Whereas the former merely inform companies where to find the most obvious gaps in their security, the latter will also expose issues that lie below the surface and demonstrate the actual damage that threat actors can inflict by exploiting certain flaws.
For example, the aforementioned research on penetration testing found that one in every two systems was so poorly secured that pentesters had to exploit only one type of vulnerability in order to breach the network perimeter and access the internal network. In other words, half of companies are not following best practices on network segmentation and other solutions that can stop or at least slow down attackers by ensuring that multiple steps are needed to break into valuable systems. This finding highlights the additional value of a pentest compared to a vulnerability assessment, since a vulnerability scan would have only identified the surface vulnerability, but not the impact (i.e. how this allowed the pentester immediate access to the internal network). Moreover, a pentest will reveal what attackers can actually do on the network once access has been obtained, such as what sensitive data they will be able to view. This is incredibly valuable information that organizations can only obtain through a penetration test.
Finally, these are some of the other weaknesses that Vonahi Security consultants have discovered as a result of penetration testing:
- Shared local administrator credentials amongst workstations and servers
- Man-in-the-middle attacks that expose sensitive data in transit
- Weak Active Directory domain user account credentials as a result of a password-based attack
- Disclosure of employee usernames and/or email addresses on devices (e.g. printers)
- Misconfigured all-in-one printers that contain privileged domain account credentials
- Weak passwords amongst web services including printers, servers, remote management consoles, etc.
- Spoofing attacks that trick end-user systems into authenticating, exposing sensitive credentials
- Misconfigured permissions associated with file shares and services, exposing sensitive data
All of these items are findings that a vulnerability assessment will not identify, which could make a significant difference within your organization if a security breach occurred. Using the results of a penetration test, your organization can identify ways to protect its most valuable data by reducing the number of attack vectors and accessible paths to sensitive resources and systems.
About Vonahi Security
Vonahi Security is a cybersecurity consulting firm that offers modern consulting services to help organizations achieve both compliance and security best practices. With over 30 years of combined industry experience in both offensive and defensive security operations, our team of certified consultants have experience working with a significant number of organizations, industries, networks, and technologies. Our service expertise includes Managed Security, Adversary Simulations, Strategy & Review, and User Education & Awareness. Vonahi Security is headquartered in Atlanta, GA. To learn more, visit www.vonahi.io
Stay Informed
